In today’s digital landscape, organizations face an ever-growing number of sophisticated cyber threats that can compromise their sensitive data, disrupt operations, and damage their reputation. This article will explore ThreatMon and delve into its crucial role in empowering organizations with the intelligence to protect their digital assets.
What is ThreatMon?
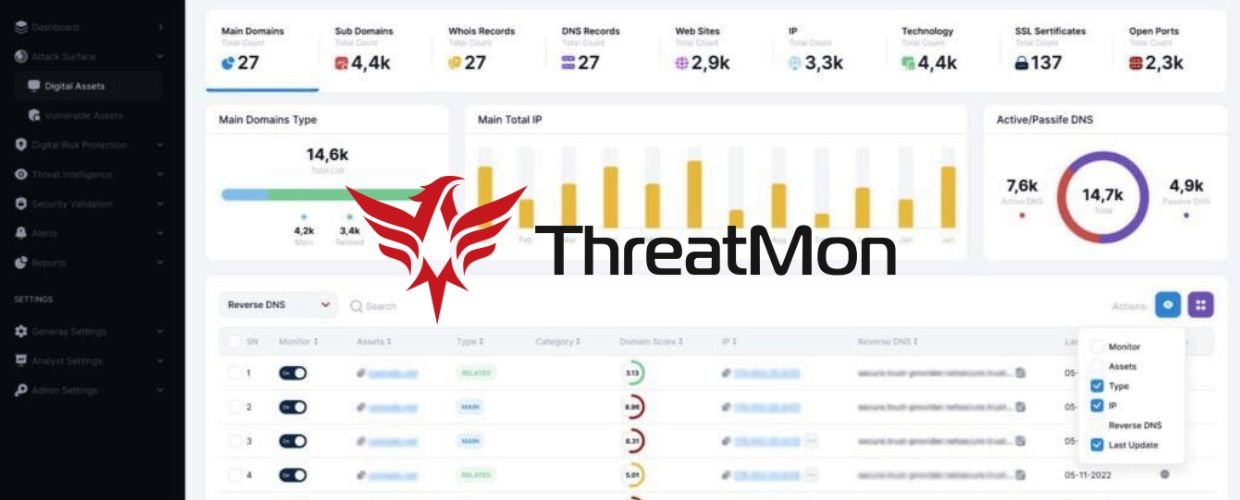
ThreatMon is a trusted name in cybersecurity, providing organizations with cutting-edge threat monitoring and detection solutions. Built on robust technologies and powered by advanced analytics, the cybersecurity platform enables organizations to detect, analyze, and respond to threats effectively.
To effectively safeguard against threats, organizations require comprehensive threat monitoring and detection solutions that provide real-time insights and proactive protection. ThreatMon is a leading provider of such solutions, offering advanced capabilities to identify, analyze, and respond to cyber threats. By leveraging artificial intelligence, machine learning, and behavioral analysis, the platform enables organizations to proactively identify and mitigate potential risks before they cause significant harm.
Key Features and Capabilities of ThreatMon
ThreatMon offers a comprehensive suite of features and capabilities designed to address the diverse security needs of organizations. Let’s explore some key components of its offerings.
Real-time Threat Monitoring
The platform provides real-time monitoring of network traffic, endpoints, and security logs to detect and alert organizations to potential threats as they occur. By continuously analyzing data from multiple sources, including network devices, firewalls, and intrusion detection systems, ThreatMon enables organizations to stay ahead of emerging threats and respond swiftly to mitigate risks.
Behavioral Analysis and Anomaly Detection
The platform employs advanced behavioral analysis techniques to establish a baseline of normal behavior for systems and users. By continuously monitoring and comparing current behavior against the established baseline, ThreatMon can identify anomalies and potential security breaches. This proactive approach enables organizations to detect insider threats, unauthorized access attempts, and other malicious activities that traditional signature-based detection systems may miss.
Threat Intelligence Integration
ThreatMon integrates with external threat intelligence feeds, enabling organizations to leverage up-to-date information on known threats and indicators of compromise. By correlating internal security data with external threat intelligence, the cybersecurity platform enhances its detection capabilities, providing organizations with a broader context to understand the evolving threat landscape and prioritize their response efforts.
Incident Response and Remediation
In the event of a security incident, the solution equips organizations with incident response and remediation capabilities. The platform provides real-time alerts, detailed incident reports, and step-by-step guidance to contain and mitigate threats effectively. Organizations can leverage ThreatMon’s automated response actions, such as quarantining compromised endpoints, blocking malicious IPs, or isolating affected systems, to minimize the impact of security incidents and restore normal operations swiftly.
Compliance and Reporting
ThreatMon assists organizations in meeting regulatory requirements by providing compliance monitoring and reporting capabilities. The platform can generate comprehensive reports and audit trails, demonstrating adherence to industry standards and regulatory frameworks. It simplifies compliance processes and helps organizations demonstrate their commitment to maintaining a secure and compliant environment.
Benefits of ThreatMon
ThreatMon offers several benefits that contribute to an organization’s overall cybersecurity strategy. Let’s explore some key advantages.
Proactive Threat Detection
By leveraging advanced analytics and real-time monitoring, the cybersecurity platform enables organizations to detect threats proactively, reducing the risk of successful attacks and minimizing the impact of security incidents.
Improved Incident Response
Its incident response capabilities streamline the response process, providing organizations with the necessary tools and guidance to respond swiftly and effectively to security incidents. It helps minimize the time to detect, investigate, and remediate threats, ensuring business continuity and reducing the potential for further damage.
Enhanced Threat Visibility
Through its integration with external threat intelligence feeds, ThreatMon provides organizations with a broader view of the threat landscape. This enhanced visibility enables organizations to make more informed decisions, prioritize their response efforts, and stay ahead of emerging threats.
Operational Efficiency
The platform automates several security processes, such as threat detection, alerting, and response actions, freeing security teams to focus on higher-value tasks. The cybersecurity platform improves operational efficiency and allows organizations to maximize the effectiveness of their security resources.
Scalability and Flexibility
ThreatMon is designed to scale with the evolving needs of organizations. Whether organizations are small or large, the cybersecurity platform can adapt to their requirements, providing the flexibility to monitor and protect their digital assets effectively.
Conclusion
In the face of increasingly sophisticated cyber threats, organizations must prioritize advanced threat monitoring and detection to safeguard their digital assets. ThreatMon is a reliable partner, offering comprehensive solutions that empower organizations with real-time threat visibility, proactive detection, and effective incident response capabilities. By leveraging advanced analytics, behavioral analysis, and integration with external threat intelligence, the platform enables organizations to stay ahead of the evolving threat landscape and protect their critical data and operations. With ThreatMon, organizations can enhance their cybersecurity posture and effectively combat cyber threats in today’s digital world.